The automotive industry is experiencing a wireless technology revolution, but if the security threat is not resolved, it may weaken this emerging market. As high-speed network connections are trying to enter the automotive arena, designers face the challenge of implementing new communication standards. Many designers who are used to the long development cycle are now competing to quickly equip new vehicles with electronic devices that users demand. To adjust time to market and navigate multiple standards, designers are turning to fpga (field programmable gate arrays). Unfortunately, as the automotive industry rushes to adopt the next-generation fpga-based car telematics system, few designers can fully understand what the fpga they choose is safe. Building a secure network begins with the design of a secure system, and the selection of the appropriate components can have a significant impact on large networks and related subscription revenues.
This article refers to the address: http://

From the engine control module to the cab interior system involving passenger comfort and safety, the car telematics system has emerged, which is a bright spot for the automotive industry and an important distinguishing point for consumers, and ultimately for oem, it It is a source of significant recurrence of booking revenue. In order to achieve the required connections to support the mobile car telematics user base, a variety of wireless transmission lines are being used in automobiles, including: 802.11, Bluetooth, terrestrial digital and satellite technologies. However, the same technology may be the starting point for its decline while implementing the automotive telematics network.
Surprisingly, security may be a top-notch factor in inhibiting the adoption of these wireless technologies on vehicles. It is a curse that vendors are unable to provide a highly secure network that is interoperable, as well as the possibility of failing to verify the device being used for payment. Oem, infrastructure developers and content providers have invested billions of dollars in car telematics, and even so, the outlook is still unpredictable. There is still a way to go to a large-scale market, and researchers predict that 10.4 million US drivers will use telematics in 2004, and that number will increase to 44 million by 2010. As shown in Figure 1, to stimulate the promotion of applications, automakers are focusing on integrating mobile devices with wireless networks. Typical applications include the integration of cellular phones via Bluetooth and interfaces into a pda (personal digital assistant) or laptop capable of wireless communication. Consumer demand for hands-free calling and computing is not only driven by convenience factors, but also driven by security issues and strict legislation.
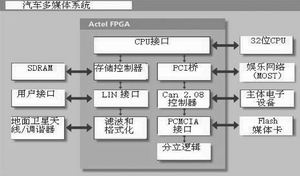
Figure 1 An fpga-based automotive telematics system allows designers to standardize a single tamper-resistant hardware platform. The platform can be customized, and the product version can be determined on a large scale at the end of the manufacturing cycle. More importantly, the dealer can be upgraded on site after being sold.

Figure 2 As Bluetooth technology moves into automotive applications, security requirements are becoming increasingly important. Fpga provides a cost-effective way to implement hardware-encrypted solutions for current data channel protocols.
In addition to basic comfort and security applications, a new area of ​​choice that promises a permanent change in the future of wireless computing is being promoted. Wireless peer-to-peer electronic payment systems will be widely used for parking and toll services and even for off-board restaurants and gas stations. Satellite radio and streaming content will quickly be welcomed, exceeding anyone's expectations. Wireless networks such as Bluetooth can be used to link several systems within the car, such as powertrains, braking systems, shock absorption systems, and rear seat entertainment systems, in order to make the smart car concept go beyond teletype control, using diagnostics. Technology and other data transmission technologies.
Advanced Express applications, competitive product versions, and shorter time-to-market have combined the benefits of fpga with the needs of telematics developers. Designers can now use fpga based on three different technologies: static random access memory (sram), flash (flash), and anti-fuse (antifuse).
Sram-based fpga represents the largest market share, but it is also the most insecure fpga architecture currently in use. Due to a volatile storage technology, such devices must be initialized or set up at power up. Although these features make sram-based fpga easy to change programming, it also poses significant security risks, such as service rejection, cloning, or reverse design. Fpga based on candidate non-volatile technology, such as antifuse or flash, provides a more secure solution. Unlike sram-based fpga, such non-volatile devices do not require a bit stream when powered up. Instead, they can be safely set up before being shipped as a final product. To protect your system from unauthorized intrusions, modifications, and tampering, it is important to understand the benefits and potential risks of all programmable architectures. For example, a hacker can disable a user authentication mechanism in a sram-fpga-based satellite broadcast console receiver, thereby allowing some unregistered users to access the service without paying. This will have a serious impact on the company's subscription-based revenue model.
The increasing number of wireless communication protocols implemented in fpga for automotive telematics offers new opportunities for experienced hackers. Bluetooth is generally considered to be sufficiently secure for small ad hoc networks, but is Bluetooth safe enough for larger mobile networks or for the transmission of remittances and other sensitive information? The Bluetooth encryption scheme seems to have some weaknesses. This string of 128-bit key length passwords can be cracked in some cases using conventional "powerful" attacks. The use of pin codes during the initialization of two Bluetooth devices is also a potential security issue.
The solution to these vulnerabilities lies in the secure fpga technology. Secure fpga can be used as a tool to implement hardware encryption to protect all important point-to-point processing, as shown in Figure 2. However, it can only be implemented if the solution has a clearer and unintelligible description. Designers need to be aware that configurable fpga systems are extremely vulnerable to cracking encryption. For example, an intruder can break the encryption mechanism by intercepting the bitstream within the sram-based fpga, and then clone the device and system to make a copy, allowing unlimited access to paid services. The system uses a programmable flash-based fpga, which provides a much more secure solution.
In addition, the Wi-Fi standards organization has recommended new standards to bridge the security gaps in the original agreement. The new ieee 802.11i is a security standard that further enhances the authentication and implementation of the wi-fi protected access security specification developed by iee in conjunction with the wi-fi alliance. Encryption effect. Most notably, the new ieee 802.11i adds a ground-up encryption standard called the advanced encryption standard (aes), and it can be secured in non-volatile fpga technologies such as flash or antifuse. Execute without worrying about direct physical leaks. Sram-based fpga is not suitable for this type of application, because countermeasures can be broken by denying various service intrusions. There is a case where the sram-based portable device can be taken offline by using the battery-depleted dos scheme by introducing the affected bit stream to the device.
Perhaps the most worrying situation is the increasing threat of design theft and Internet security. In particular, once system security is compromised, it is not difficult to use malicious or criminal technology to make large amounts of consumption. The most effective protection for patented designs is the use of antifuse or flash-based fpga to protect wireless networks and car payment service gateways. More advanced security measures can be implemented on higher-level systems and networks only if basic design security issues are raised at the component level.
The Substation Fitting is mainly used for the connection of the bus down-lead of substation and the outlet terminal of electrical equipment (such as transformer, circuit breaker, isolating switch and mutual inductor). Because the outlet terminal of electrical equipment commonly made by copper and aluminum, while the bus down-lead is divided into aluminium strand wire or steel core aluminum strand wire, the equipment, by material, was into the aluminum and copper two series. According to the installation method and structure of the different equipment, the line clamp was divided into bolt type and compression type. Each type of wire clip is divided into three, listing as 0, 45 and 90 degrees according to the angle of the down-lead and the installation of the terminals from the electrical equipment.
Substation Fitting
Grid Line Fitting,Power Fitting For Substation,Transmission Line Hardware,Substation Cable Fitting,High Voltage Connector ,Insulated Clamps ,Straight Line Clamp
Jiangsu Chuandu Electrical Technology Co.,Ltd. , http://www.cdepf.com