It is reported that after a few days of outbreak, the ransomware did not stop it from ravaging. At this time, however, Microsoft users finally responded and began to take some rescue measures against the virus. However, in the face of the new WanaCrypt0r 2.0 ransomware, the virus software based on the hacking technology of the National Security Agency (NSA) did not work well.

In March, Microsoft had just successfully completed the NSA tool EternalBlue (Eternal Blue). Today, Windows also updated Windows Defender antivirus and Windows Security Essentials security tools in the face of WanaCrypt0r ransomware that was distributed via EternalBlue.

For the ransomware virus, needless to say, after a week of discussions on the Internet, the virus has been fully understood, in fact, is to allow users to open the file, do not pay the money to delete the file threats. At this time, the small partner who has the habit of backup should be pleased. Even if the file is locked, I still have a backup. If you want to delete it, delete it.
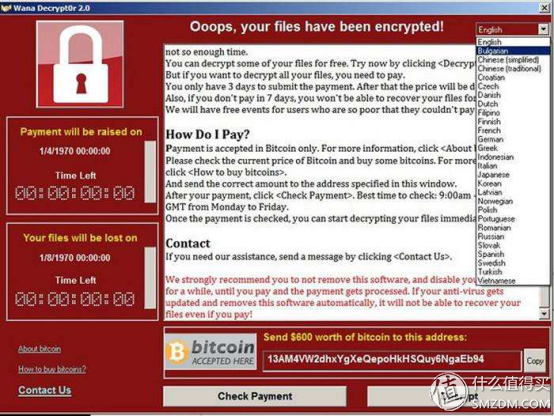
It is true that ransomware is arguably the hackers' speculation, and can even blame the business model inherent in the Microsoft version. However, do we not have a little responsibility for this incident? The bad habits of using computers on weekdays; not having a good sense of protection; and not having a backup plan for losing files, isn't it also an invisible disaster?
(I) Safety Awareness
For most small partners using computer guru, this kind of consciousness is an intangible thing that nobody can see. It is naturally easy to forget. Even though many users now know that the virus is spread by social media, untrusted sites, downloaded location resources, spam, etc., many people will still abandon “inquiries†if they do not know the source of the data. The principle of "dead cat" wants to find out.

(II) System Security
What system is your computer now? If the computer hardware is still available (if it is old or not, please install a win7 or later version). If you don't understand it, try not to make too much of the original system. The self-arranged, do not write in the OEM version system (brand machine pre-installed system), or choose the original system, personal use to use the home version, do not have to install the ultimate version. Try to install 64-bit.

(III) System Application
Please select the software that is biased towards a single function according to individual needs, and pay attention to upgrading the software to the latest stable version. The browser uses a modern browser, such as chrome, Firefox, IE (the latest version). If it is Windows 10, use its own browse. Device. Do not install the system optimization software indiscriminately, security protection does not need to be installed, win10 comes with protection, win7 leave MSE like.
1. File Encryption: TrueCrypt

TrueCrypt is a free open source encryption software that supports Windows Vista, 7/XP, Mac OS X, Linux and other operating systems0. The software can directly create a virtual disk on the hard disk, without generating any files, providing a variety of encryption algorithms including: AES-256, Blowfish (448-bit key), CAST5, Serpent, Triple DES, and Twofish, and other features. There are support for FAT32 and NTFS partitions, hidden volume labels, hotkey booting, and more.
2. Firewall: netlimiter (pay, optional)
NetLimiter is a network traffic control software running on Windows 98/98SE/me/2000/xp/2003. Through it, you can directly control each program's access to the Internet and traffic distribution.
3. Password management: keepass
KeePass Password Safe includes a powerful password generation engine and cryptographic storage to provide a secure password storage space. When you start using KeePass Password Safe, you must first determine a starting password (remember to remember this password). This password is used to identify the user, using KeePass Password Safe software.
4. Virus protection: MSE
Microsoft Security Essentials is a free anti-virus software developed by Microsoft Corporation. The software can provide protection for genuine Windows XP, genuine Windows Vista, and genuine window7.
5. File backup: Baidu cloud, nut cloud can be.
6. File Recovery: Data Recovery Software/EasyRecovery
Mutual Shield Data Recovery Software is a universal data recovery software that supports data recovery of various devices such as computer hard disks, mobile hard disks, USB flash drives, mobile phones, cameras, SD cards, etc. The recovery function is erroneous to delete file recovery and formatted hard disk recovery. , U disk cell phone camera card recovery, error recovery empty recycle bin recovery, hard disk partition loss / damage data recovery, universal recovery, delete files via ransomware can use the software for data recovery.
Finally, we must also pay attention to our own operations. People are the most fickle animals, the possibility of misuse is quite high, please do not use any place where you need to enter a username/account number password, keep a look out for popular fonts or security warnings; do not believe/connect with any software from unknown sources, Hot spots; if there is any mention of related information leaks or loopholes in the news, please suspend use, or change your password.
Rectifier bridge is to seal the rectifier tube in a shell. Points full bridge and half bridge. The full bridge connects the four diodes of the connected bridge rectifier circuit together. The half bridge is half of four diode bridge rectifiers, and two half bridges can be used to form a bridge rectifier circuit. One half bridge can also be used to form a full-wave rectifier circuit with a center-tapped transformer. Select a rectifier bridge to consider. Rectifier circuit and operating voltage.
Bridge Rectifier,Original Bridge Rectifier,Full Bridge Rectifier ,Diodes Bridge Rectifier,Single Phase Rectifier Bridge, Three Phase Bridge Rectifier
YANGZHOU POSITIONING TECH CO., LTD. , https://www.cnchipmicro.com