Three key considerations for designing low-power Bluetooth beacons quickly, safely and efficiently. This information discusses the three major issues of hardware, software, and battery life that beacon designers need to consider.
In this article, we will focus on the beacon designer's consideration of security and privacy in addition to considerations such as hardware, software, and battery life.
Will the beacon track your every move?
Recent news reports emphasize that consumers are concerned that beacons will "track their own every move." In fact, typical beacons do not collect data because they are one-way devices—only broadcast. What really invades people's privacy is the smartphone, which infringes people's privacy by knowing the location of the beacon and the services provided by the app on the phone.
In fact, smartphones can invade your privacy by using GPS, Wi-Fi, and cellular networks without beacons. Just because beacons can be deployed in a low-power and low-cost way, while implementing a new application model, it also raises some reasonable concerns that have long existed. Keep in mind that users can also turn off all of these "LocaTIon Based Service" in their device settings.
IT professionals and business people are also concerned about the security risks of beacons. However, this again implies the functionality that beacons do not normally have: they are usually one-way devices that can send but cannot receive information. That is to say, the security of beacons is important in some applications, not only for the operations that are running, but also for the deployment of beacons.
For beacon broadcasts, it is not encrypted by definition unless it is part of a proprietary network. However, IT professionals need to protect incoming beacon network traffic (if any) with the same level of protection they provide for the rest of the network, or at least to the extent that the beacon hardware can accommodate it.
In some beacon applications, proximity beacons may have real value, such as getting bonus points or entering a store, so beacon providers may also need to implement preventive fraud protection. This may include a timestamp, a temporary ID, or a random security key, which is generated with each proximity event and verified by the backend system.
Device management function security
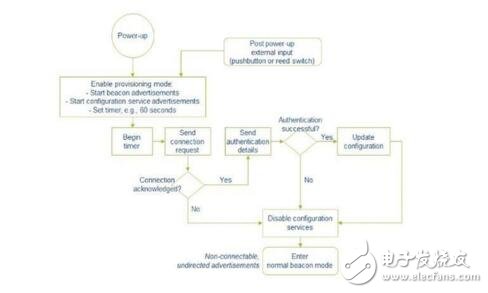
When a beacon is deployed or upgraded in the field, it undergoes a configuration process. This is probably the time when the beacon is most vulnerable to security breaches. In these cases, beacons can use Bluetooth security features (such as pairing, authentication, encryption, etc.), as well as other security measures such as strong password protection.
For deployment, the access configuration service can be limited to a short time window. At the end of the window, the device becomes a normal broadcast beacon and no longer broadcasts its internal services. The process is shown below:
Beacon developers need to pay attention to
1) Choose a widely used and proven Bluetooth stack. Since the beacon is new, the new entrant may spread the FUD (negative concept). The buyer is wary. Choose a company that understands low-energy Bluetooth and adopt a market perspective.
2) Choose a company with proven software development tools. Software development requires more than just editors and debuggers. It also needs to include mature sample code for common use cases, a scripting engine for common commands, and a thoughtful API for the final transition from one standard revision to another. These tools will work together to speed up the development process.
3) Choose a company that provides good customer support. This is closely related to market-proven stacks and software tools; if selected companies have been market-proven, they will have support forums with hundreds of questions and answers about hardware and software, a large user base and waiting for answers. Support staff for new issues, a range of different product combinations for different applications, and more.
100V eVtol Battery,100V Battery Pack,100V Battery,100 eVolt Battery
Shenzhen Jentc Technology Co., LTD , https://www.phenyee.com