Previous cognition
I have just been in contact with the IT industry before, and as an operation and maintenance, I thought that the security I need to do is to modify the server password to be complicated, the ssh port is changed to non-22, and there is no need to log in to the server to guarantee my maintenance. Things are safe.
Current cognition
I have been working for several years. In this battle, I encountered a server hack, the website was attacked by DDOS, the database was tampered with, and so on. The server is not that you don't let people do not let people on, so the topic of IT security is still relatively heavy, involving a lot of things, only you know more, you will know that the security you know is actually so less.
Let me talk about IT security.
1, network security
Many of our companies and environments do not use third-party auditing systems, fail to fractal based on recorded data, and generate audit reports. In fact, the audit system is very important, and it can be traced back to the operation, which is much more useful than what you say. My company is actually buying a log audit system, but it is an egg. In terms of operation and maintenance, I built an ELK for tracing the operation of the server and monitoring the system log and security log. This has completely reached my point of thinking. The effect, the other system-related logs, the developers themselves have ELK systems, they are used to monitor the behavior of the app, but also for auditing.
Here is my own ELK system for monitoring server operations:
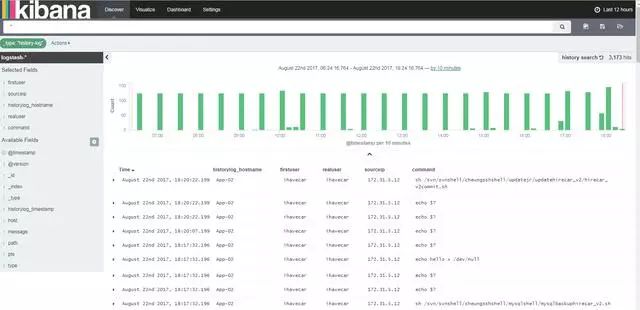
In fact, the network security is very wide. For example, you can wake up the device with ARP binding, which can avoid arp attacks, etc. You can also purchase intrusion detection devices, intrusion prevention devices, firewalls, etc., network devices periodically change passwords, network devices. Configure the authentication failure login processing function, configure the operation timeout and other functions, and try to use the https protocol to encrypt the transmission.
In addition to the above, regular self-tests (vulnerability scanning, weak password scanning, baseline configuration information, etc.) should be performed to scan and discover host ports, weak passwords, and security vulnerabilities, and scan and discover known business application vulnerabilities. Knowing Trojans for scanning and discovery, analyzing and submitting scan results to promote business security management and security issues
2, host security
In most of the current companies, the operating system does not install the host intrusion detection system, and fails to detect the intrusion of important servers. It can record the source IP address, attack type, attack target, attack time, etc. of the attacker. Provide an alarm when a serious intrusion occurs. Many people say that this requires the purchase of hardware WAF or intrusion prevention equipment. This is indeed a small expense. The average company can't afford it, like us, can't afford it. But it does not mean that we have no choice. We can install real-time detection and killing of malicious code software products in the operating system, real-time detection and killing of malicious code, such as OSSEC and HIDS, these products are free and open source.

Host security also includes system configuration security, authentication security, and more. For example, the operating system provides identity authentication measures, configures the authentication failure processing function (that is, the number of failed login attempts, which can effectively prevent malicious cracking), and strengthens the password complexity requirement. On the original basis, it should not contain common character combinations, digital combinations, Predictable password combinations such as keyboard order, important server use resource mandatory access control policies (such as user, process, file kernel level protection), limit the access rights of the default account, modify the default password of these accounts, if conditions permit, should be heavy Name the default account;
3, application security
a), the proposed application system uses two or more combination mechanisms for user identity authentication;
b), it is recommended that the application system limits the complexity of the account password, the password length is limited to 8-20 digits; the password is required to be at least two combinations of numbers and alphabetic characters, and the password password period is not more than half a year;
c) It is recommended that the application system enable the login failure processing function, the number of restrictions is not more than 5 times, and the account processing is performed for the login failure user;
d), the recommended application system should enable the user identity authentication information complexity requirements and login failure processing functions;
e) It is recommended that the application system set sensitive tags for important information resources. If the system does not support setting sensitive tags, special security devices should be used to generate sensitive tags to support the mandatory access control mechanism.
f), it is recommended that the application system open the security audit function, and the security audit scope covers each user and its related operations;
g), it is recommended that the application system enable the security audit function, and the audit function cannot be interrupted and the security record cannot be deleted, modified or overwritten by the non-administrator;
h), it is recommended to limit the number of concurrent session connections of the application system for a period of time;
i) suggesting that the application system limit the maximum limit of an access account or a request process;
j), suggesting that the application system provides a service priority setting function, setting a priority of accessing an account or a requesting process according to a security policy, and allocating system resources according to priorities;

4, data security and backup recovery
a) It is recommended to provide off-site data backup function, and use the communication network to batch transfer key data to the alternate site at regular intervals;
b) It is recommended to provide hardware redundancy of major network equipment, communication lines and data processing systems to ensure high availability of the system;
c), data development, test environment If you want to import production data, you need to specify the data desensitization process to desensitize sensitive personal information, such as bank cards, mobile phone numbers, etc.
d), data access must have a strict process, if the non-operation and maintenance personnel want to access the data, after completing the permission application process, he can be given permission to read, but can not give him the right to back up the data to the local, The operation can be restricted by the Windows bastion machine, and the administrator can disable the clipboard of the person;
e), the database should be upgraded once a year, even if your database is placed on the intranet, but you can not guarantee that your developer's code will not be hacked, as long as the code is invaded, or is implanted in the back door, you can pass you The program is scanned into the database. Database vulnerabilities can be more than one or two. Basically, a stable version of the database can have about 30 high-risk vulnerabilities and about 50 medium-risk vulnerabilities. These vulnerabilities are not solved by patching. The best way is to upgrade to a stable version of the latest version of the database;

5, web business security
a), should set a reasonable session timeout threshold, reduce the session timeout threshold as much as possible within a reasonable range, can reduce the risk of session hijacking and repeated attacks, destroy the session immediately after the session timeout threshold, clear the session information ;
b), should limit the number of concurrent connections in the session, limit the number of concurrent connections of the same user, to prevent malicious users from creating multiple concurrent sessions to consume system resources, affecting service availability;
c), to ensure the security of the sensitive information communication channel, it is recommended to use SSL between the client and the web server. And correctly configure SSL, it is recommended to use SSL3.0/TLS1.0 or higher, the symmetric encryption key length is not less than 128 bits, the asymmetric encryption key length is not less than 1024 bits, and the one-way hash value is not less than 128. Bit
d) The scope of the log record should cover important events such as key operations, important behaviors, and usage of business resources for each user. Such as normal user abnormal login, release of malicious code, abnormal modification of account information, and the key operations of the administrator in business functions and account control;
e), the web program should be coded before or after the upgrade, form a report, and update the code for the audited problem;
f), the password transmission user password should be prohibited, it is recommended to use SSL encryption tunnel to ensure the security of user password transmission;
g), to respond to key business operations, such as modifying user authentication and authentication information (such as passwords, password retrieval questions and answers, binding mobile phone numbers, etc.), need to be authenticated twice to avoid fraudulent use of user identity, User caused losses;
h), should avoid the authentication error prompt leak information, when the authentication fails, should provide the user with a common error message, should not distinguish between account error or password error, to avoid these error message is used by the attacker;
i) should support password policy settings, support mandatory password policies from the business system level, including password length, complexity, replacement cycle, etc., especially the administrator password of the business system;
j), should support the account lockout function, the system should limit the number of consecutive login failures, after the client fails multiple attempts, the server needs to lock the user account for a short time, and the lock policy supports the configuration unlock time;
k), session protection measures should be taken to prevent the session between the software and the server from being tampered with, forged, replayed, etc.;
The KSPOWER brand constant voltage led driver provides L series with 4 functions optional: 5 in 1 dimmable(0-10V/1-10V/Triac/PWM/resistor), non dimmable, triac/phase-cut dimmable, 4 in 1 dimmable(0-10V/1-10V/resistance and PWM signal) constant voltage LED Drivers; N series phase dimmable LED driver; E series junction box LED driver and P series LED Driver. The constant voltage driver is IP65 IP67 NEMA 3R IP20 rated environment protection for indoor and outdoor LED lighting, with or without junction box for easy installation. The led grow light driver is Class 2 Class P rated and high built-in PFC function, offers 5 years after-sale warranty and both ETL/cETL, UL/cUL, FCC CE ENEC GS RoHS Listed and SELV style enclosures. The led electronic driver transformers offers outstanding led dimming and power performance, flicker free and protections for short circuit, over load, over voltage and over temperature. The P series LED driver compact small plastic unit size for built-in LEDs.
Power Led Drivers,Led Ac Driver,landscaping transformer,led electronic driver,led grow light driver
Shenzhenshi Zhenhuan Electronic Co., Ltd , https://www.szzhpower.com